BGP AS-Override Risks
One of BGP’s loop prevention mechanisms is to deny the installation of a route that contains a router’s own AS in the AS-PATH. This is very effective on networks such as the Internet. Using the as-override feature on the Internet can be disastrous!
However, within a controlled private network, such as an MPLS network that a single ISP manages, BGP AS Override might be safe to use but it depends on the topology.
For example, with a simple topology like this one:
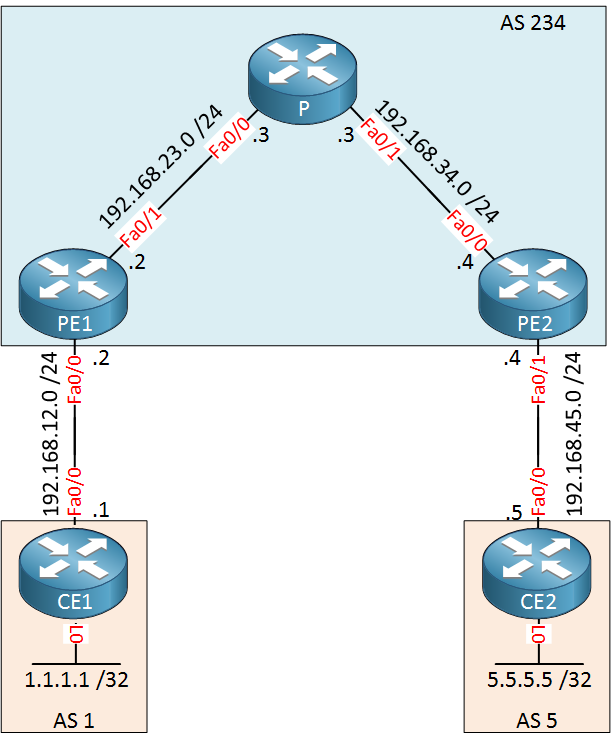
The topology is like a tree where the customer ASes hang below the SP.
In such a topology, there is no case where you would have a series of ASes in a loop arrangement. As a result, using the as-override is safe in such an environment.
However, if the customers are multi-homed to PE routers or have a backdoor link between different customer sites, it's another story. Make sure you are careful with AS-override and configure additional filtering if required.
Links
https://networklessons.com/bgp/mpls-layer-3-vpn-bgp-override