Network Tunneling
A "tunnel" in networking is characterized by the encapsulation of one protocol within another. This is typically performed at the same or a higher layer of the OSI Model as opposed to the process encountered during normal encapsulation.
This process enables the transfer of Protocol Data Units (PDUs) across a network without utilizing the information contained in their headers. While they are encapsulated within the tunnel, they are considered payload data, and have no affect on their transmission while encapsulated. Once the PDU exits the tunnel, it is then processed using the information found within its header, utilizing standard protocols.
The following is an example of a tunneled packet, where the original IP packet is encapsulated within an Authentication Header (AH) used by IPSec, and a new IP header is prepended to the original packet.
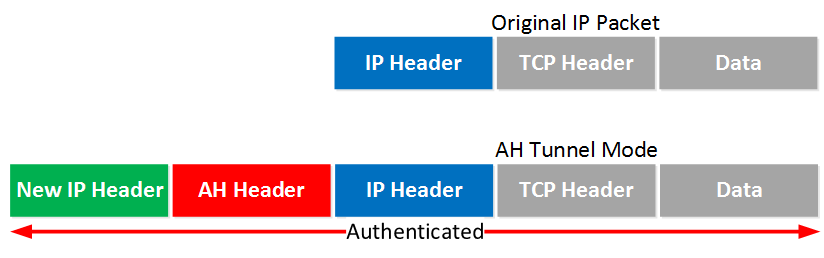
In this way, the original IP packet and its header are not involved at all in the transport of the data as long as they are encapsulated within the new IP header. Once the packet exits the tunnel, the new IP header and the AH header are removed, and the packet transmission continues using the original IP header.
Examples of Tunneling
The following is a list of protocols and mechanisms that are used in networking that deliver some form of a network tunnel. The list is not complete but gives a wide variety of protocols and methodologies that adopt the term "tunnel."
- GRE
- MPLS
- IPSec
- VXLAN
- VPN
- QinQ
- L2TPv3
- LISP
- MPLS TE - TE Tunnels
- Wireless - CAPWAP tunnel
- IPv6 6to4 tunneling
- IPv6 ISATAP
Tunneling and Security
Furthermore, tunneling is associated with security considerations when packets are encapsulated within security headers, such as those provided by ESP and AH. While traditional tunneling involves encapsulation across OSI layers, security tunneling focuses on adding security headers without necessarily changing the OSI layer.
In cases like IKE phase 1 and phase 2, tunnels do not involve layering encapsulation but signify security encapsulation, thus fitting the broader notion of tunneling in networking.
Links
https://networklessons.com/security/l2tpv3-layer-2-tunnel-protocol-version-3
https://networklessons.com/ipv6/ipv6-isatap-intra-site-automatic-tunnel-addressing-protocol
https://networklessons.com/switching/802-1q-tunneling-q-q-configuration-example
https://networklessons.com/security/encrypted-gre-tunnel-with-ipsec
https://networklessons.com/ip-routing/how-to-configure-gre-tunnel-on-cisco-ios-router
https://networklessons.com/ipv6/how-to-configure-ipv6-automatic-6to4-tunneling
https://networklessons.com/ipv6/how-to-configure-ipv6-tunneling-over-ipv4
https://networklessons.com/mpls/mpls-vpn-over-mpls-te-tunnels