Why do we trust a website certificate
When you go to a HTTPS website, you probably see that the website has a valid certificate. For example, here is Networklessons.com:
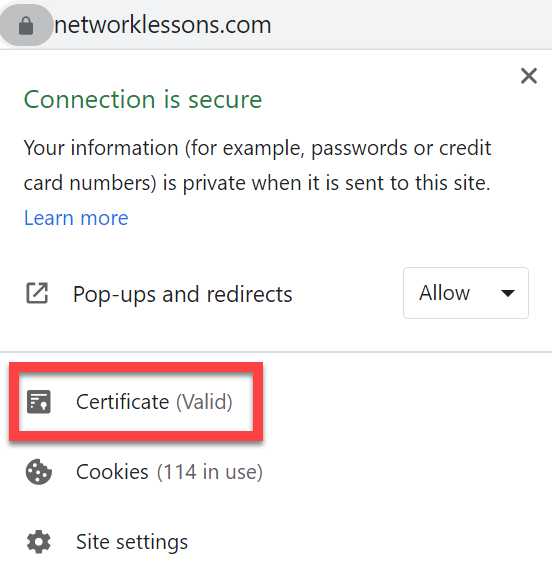
It shows up as "valid". Why do we trust this certificate?
Take a closer look at the certificate:
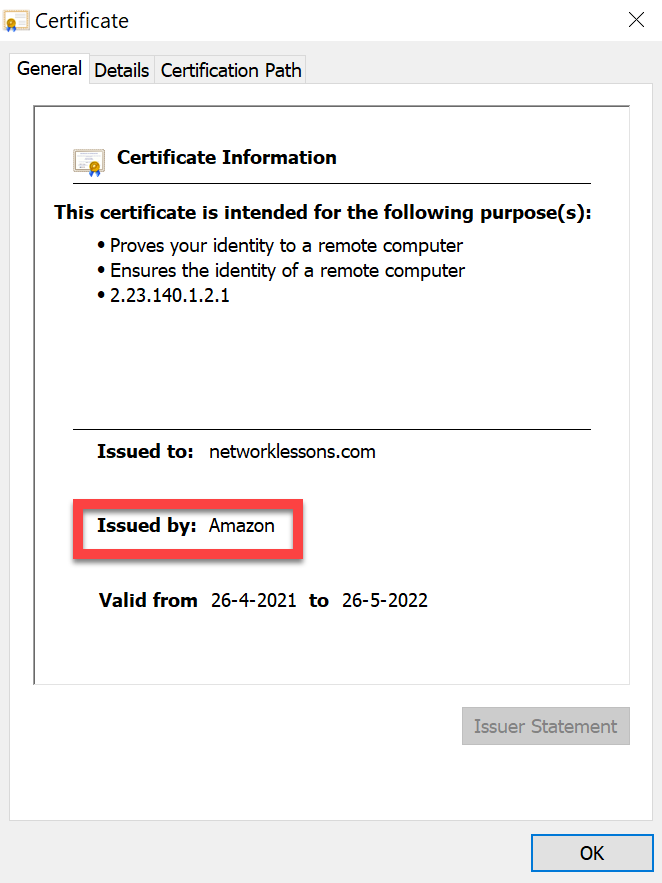
The certificate is signed by Amazon. Why do we trust Amazon? Take a look at the Certification Path:
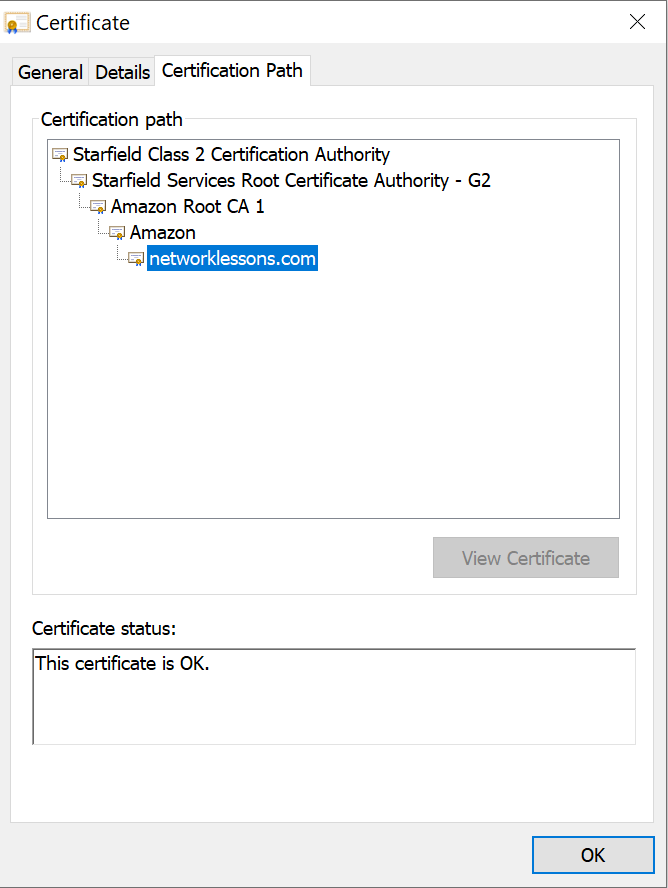
We see multiple Intermediate CAs in between and on top is the Root CA (Starfield Class 2 Certification Authority). We can take a closer look at this certificate:
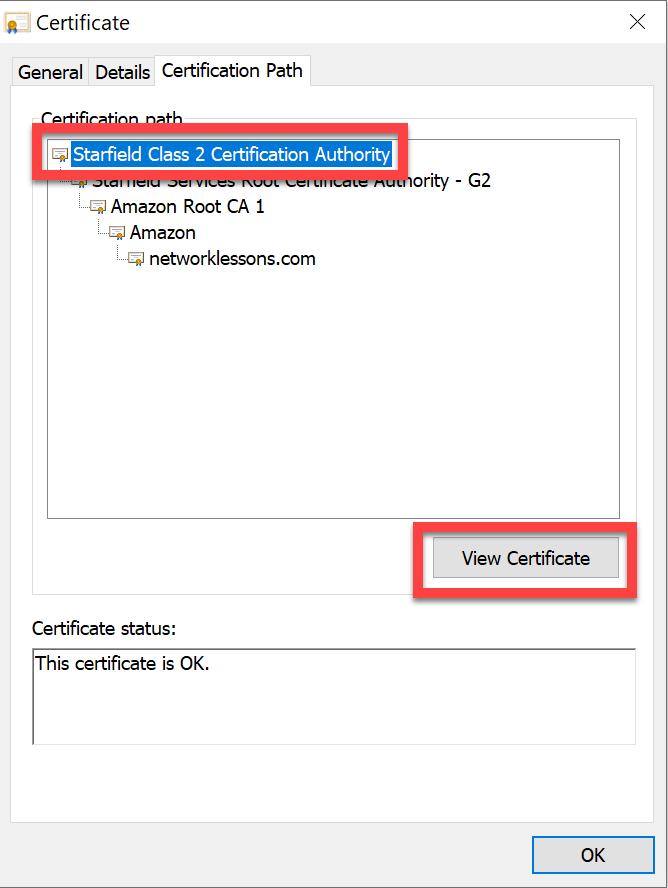
The certificate shows up as "OK":
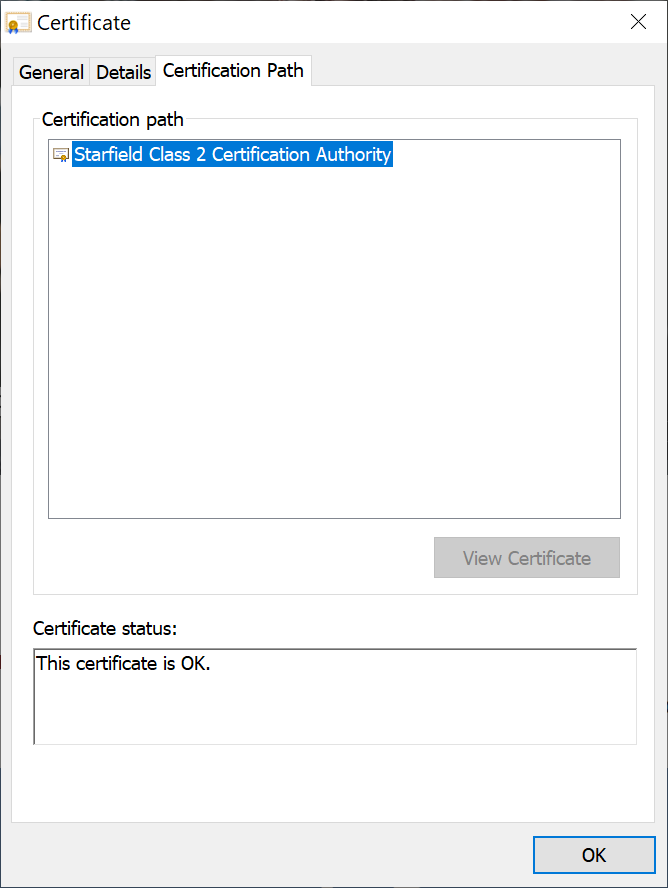
Why do we trust "Starfield Class 2"? To answer that question, we open control panel on Windows and look for "Manage computer certificates":
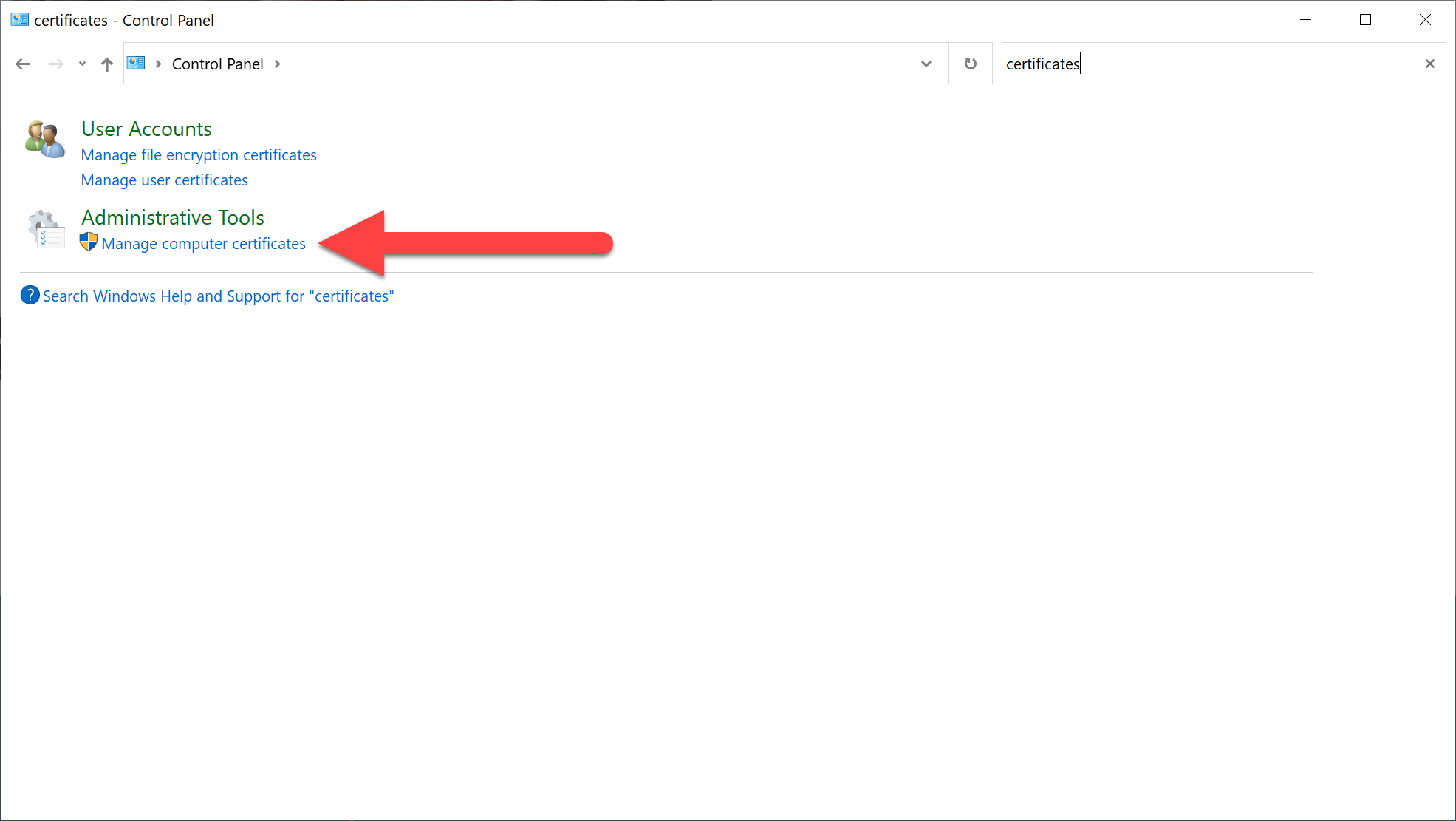
Look for the Trusted Root Certification Authorities and scroll down until you find "Starfield Class 2 Certification Authority":
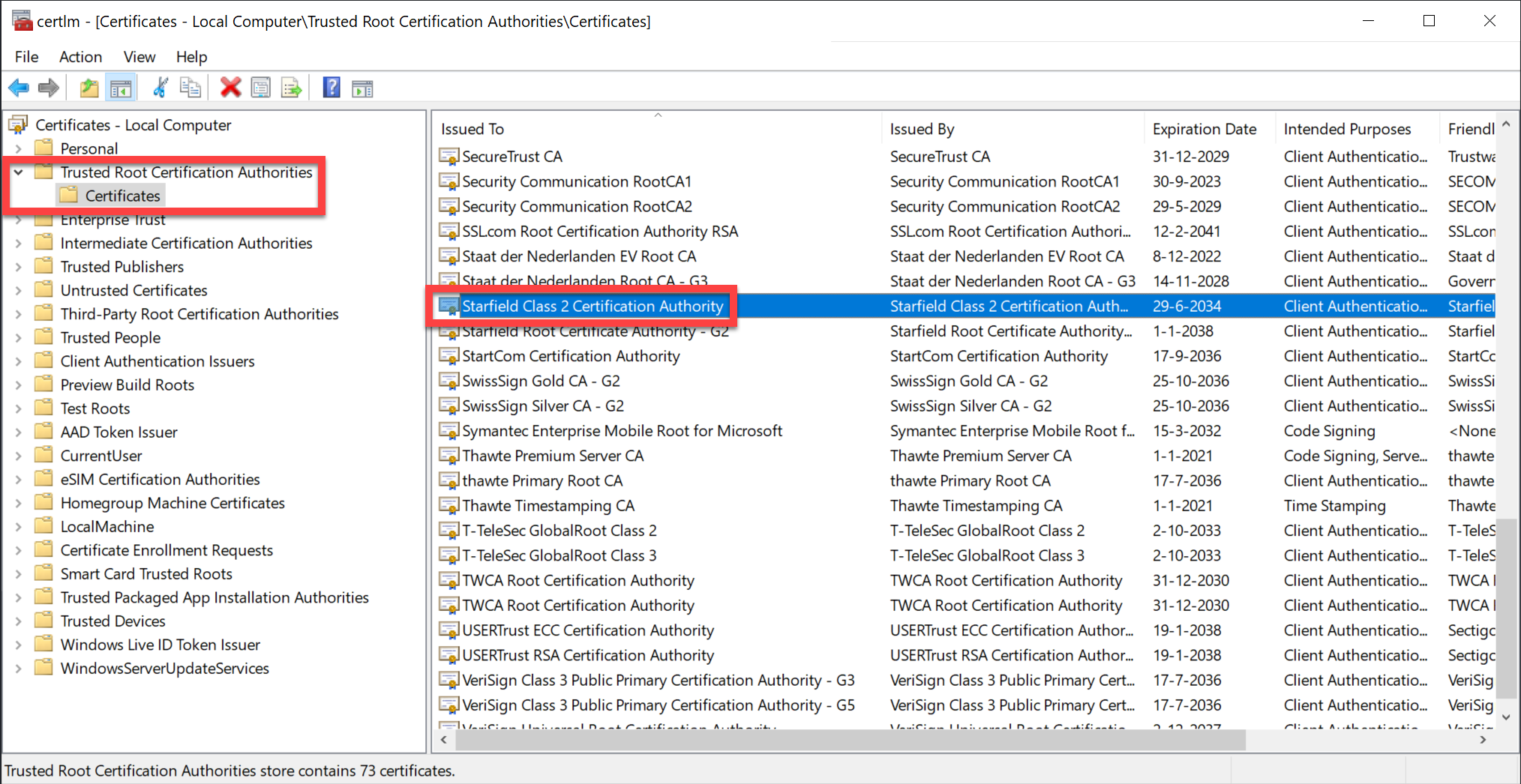
There it is. The reason we trust this certificate is because it's pre-installed on Microsoft Windows.
Microsoft has a "Microsoft Trusted Root Program" where they decide what root certificates become pre-installed.
The reason you trust the networklessons.com certificate is because:
- The networklessons.com certificate was signed by an intermediate CA from Amazon.
- The Amazon intermediate CA certificate was signed by the intermediate CA "Amazon Root CA 1".
- The Amazon Root CA 1 certificate was signed by the intermediate CA "Starfield Services Root Certificate Authority - G2".
- The Starfield Services Root Certificate Authority - G2 was signed by Root CA "Starfield Class 2 Certification Authority".
- We trust Root CA "Starfield Class 2 Certification Authority" because it is pre-installed on Microsoft Windows 10.
Links
https://docs.microsoft.com/en-us/security/trusted-root/program-requirements