IPSec - Key Exchange Data
During the exchange of data in phase 1 of an IPSec communication, IKEv1 is used to exchange key data. In particular, the key exchange data found within the following Wireshark capture.
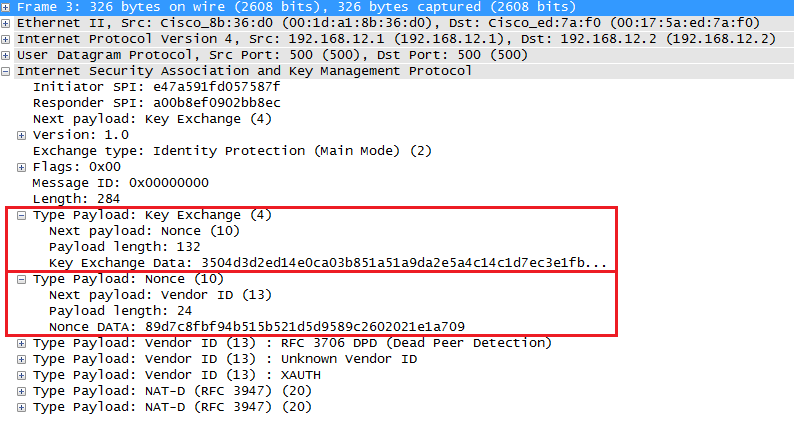
Yes, the Key Exchange Data contains the public key of the device that sent the packet. This public key is then used by the receiving device, in combination with its own private key, to derive the shared secret key material. This shared key material is then used to generate encryption and authentication keys for the IKE SA and the subsequent IPsec SAs established during IKE Phase 2.
In the above capture, you can also see the nonce that is exchanged. The nonce is not actually directly used for authentication. Instead, it serves as a cryptographic input to derive keying material, to protect against replay attacks, and to ensure the uniqueness of keying material for each security association. It is used in conjunction with the DH key exchange, however, DH and the nonce serve different purposes in the protocol.
The Diffie-Hellman key exchange is used to establish a shared secret between two parties (initiator and responder) without disclosing it to potential eavesdroppers.
Nonces, on the other hand, are random or pseudo-random numbers generated by each party in the IKE protocol. They serve multiple purposes as described above.
How are these related? In the IKE protocol, both the Diffie-Hellman shared secret and the nonces generated by the initiator and responder are used as input to a key derivation function (KDF), along with other cryptographic parameters. The KDF generates the keying material for the IKE Security Association (SA) and the subsequent IPsec SAs. By using nonces together with the Diffie-Hellman shared secret, the protocol ensures that the derived keying material is unique for each SA, even if the same devices establish multiple SAs.
Links
https://networklessons.com/cisco/ccie-enterprise-infrastructure/ipsec-internet-protocol-security/